- Broker
- Fees
- Deposit
- Withdrawal

Quotex review 2023 – Is it a scam or not? – Test of the broker
- Min. deposit $10
- $10,000 demo
- Professional platform
- High profit up to 95%
- Fast withdrawals
- Signals
Trading Binary Options can bring you very fast profits or high losses. Many traders are interested in using this financial product. So it is very important to invest with a reliable online broker. Quotex.io, Quotex.com, or qxbroker.com is a new trading platform that offers such kinds of services.
In this review and test, I will check Quotex for you and tell you the truth about this binary broker. What are the trading conditions, how is the platform working, and how fast can you payout your profits? I will answer all the important questions for beginners with Quotex. Should you trust this broker and invest money there? Is it a scam or not? – Find out in my honest Quotex review.
(Risk warning: Your capital can be at risk)
Quick facts about Quotex:
| ⭐ Rating: | (5 / 5) |
| ⚖️ Regulation: | IFMRRC (International Financial Market Relations Regulation Center) |
| 🏛 Founded: | 2020 |
| 💻 Trading platforms: | Web platform, mobile applications |
| 💰 Minimum deposit: | $10 |
| 💱 Account currencies: | USD, EUR, GBP, BRL, IDR, MYR, INR, KZT, RUB, THB, UAH, VND, NGN, EGP, MXN, JPY |
| 💸 Withdrawal limit: | No limit |
| 📉 Minimum trade amount: | $1 |
| 📈 Maximum trade amount: | $1,000 |
| ⌨️ Demo account: | Free and unlimited |
| 🕌 Islamic account: | Yes |
| 🎁 Bonus: | Up to 100%+ Use the code ‘BObroker50’ to get a 50% deposit bonus |
| 💎 Yield: | Up to 95%+ |
| 📊 Assets: | 100+ forex, stocks, commodities, indices, crypto |
| 💳 Payment methods: | Credit cards, e-wallets, online banking, cryptocurrencies |
| 🧮 Fees: | No additional fees |
| 📞 Support: | 24/7 chat and email |
| 🌎 Languages: | More than 20 |
(Risk warning: Your capital can be at risk)
What is Quotex? The broker presented
Quotex is a new digital options broker for investing in more than 100 markets. The platform was founded in 2020 and is managed by the Maxbit LLC (owner) with the address First Floor, First St Vincent Bank LTD Building, James Street, Kingstown, St. Vincent und die Grenadinen where you will find the headquarter of the company. It is a typical offshore broker that accepts all types of clients. You can trade on the markets by getting a high yield of up to 95%, which means you invest $100 in a rising EUR/USD chart, and if you are right in a certain time period you will earn 5. Later I will go into detail to show you how exactly it works.

The broker for online trading presents a newly developed trading platform and software. The platform is available for desktop and mobile devices. The company is active in more than 20 different countries and offers support service in different languages. There is not so much information about the company on the internet because the broker is very new. But the first impressions for me are quite good. Quotex platform has good offers for clients and investors in the markets.
Watch my full video review:
(Risk warning: Your capital can be at risk)
The pros and cons of Quotex:
Due to my comparison with other trading platforms, I will show you the pros and cons of Quotex. But keep in mind, on every platform or broker; you will find some disadvantages. It is very hard to find the perfect one.
Advantages:
- Free $10,000 demo account
- Minimum deposit of only $10
- Minimum trade amount $1, maximum trade amount $1,000
- High return up to 95%
- User-friendly interface
- Huge variety of trading assets
- Fast trade execution
- Instant deposits
- Fast and secure withdrawals
- Free bonus (Use the code ‘BObroker50’ to get a 50% deposit bonus)
- Available in many countries and languages
Disadvantages:
- No phone-support
- No iOS app is available at the moment
(Risk warning: Your capital can be at risk)
Is Quotex regulated? Regulation and security of the broker
If you want to invest in the financial markets or any type of financial product, I recommend using a regulated broker and platform. Watch out for reviews like this Quotex review. It is very important for investors to have high security when investing in financial products. On the internet, you will find a lot of frauds and scams when it comes to Binary Options trading. In order to avoid a scam or fraud, you should choose a regulated Binary Options broker.
From my experience, the Quotex broker is a safe and secure online broker. I tested the platform several times, and it is my main trading broker. Deposits and withdrawals of money are working very fast. Quotex is regulated by the International Financial Market Relations Regulation Center (IFMRRC) with the number TSRF RU 0395 AA V0161. Click on the number to see the license.

The FMRRC regulation is not a regulation of an official finance authority, it is an international and independent regulator. That means Quotex is unregulated in terms of country authority regulations. In addition, Quotex is an official company with the company ID: 226716.
It seems that Quotex is a safe broker for investing. I also searched for negative comments about this trading service and I could not find any negative reviews about this broker. Furthermore, only secure and regulated payment methods are used for deposits and withdrawals. All in all, I can say that Quotex platform is a secure broker for online investments by using digital options.

- Regulated by the IFMRRC with the number TSRF RU 0395 AA V0161
- The official company number is: 226716
- Safe and secure website/platform
- 2-factor authentification is available
- Secure payment methods
(Risk warning: Your capital can be at risk)
Is it legal in your country?
You can trade through Quotex as it is a trustworthy binary options trading. This trading platform is legally registered and regulated by a trusted organization. So, you can consider Quotex as a legal way of entering the binary options market.

However, traders from all the countries cannot use its services as this platform can be operated from a a lot of countries. Some regulators forbid Quotex to operate in their country. Traders from these countries are automatically blocked by the broker.
Is Quotex legit or not?
Quotex is definitely legit and I can recommend this trading platform, especially compared to other trading platforms. The deposits and withdrawals are very fast without any additional fees. You can make money with Quotex and be safe to get it withdrawn in a few minutes or hours. I tested the broker by myself and it is very secure. Actually, I made more than $ 8,000 profit. Later in this Quotex test, you will see my withdrawal proof.

Traders from all around the world use Quotex because it’s a reliable platform. It has a transparent interface, simplicity, and unlimited features that make it one of the best mobile apps.
Is Quotex safe? – Security measures for traders and your money
When it comes to binary trading, security measures are crucial in terms of the safety of your money. Of course, you want to trade with a binary broker that protects you against data abuse and makes you feel safe. From my experience, I can tell you: Quotex does everything to maintain a high level of security for its traders. There are no worries concerning the safety of the platform itself and for you as a trader on it.
See all facts about the security:
| Regulation: | IFMRRC |
| SSL: | Yes |
| Data protection: | Yes |
| 2-factor authentication: | Yes |
| Regulated payment methods: | Yes, available |
| Negative balance protection: | Yes |
(Risk warning: Your capital can be at risk)
Review of the Quotex (QX Broker) trading conditions and offers
With Quotex you can invest in the financial markets by using Binary Options (a form of digital options). The technique is quite simple, you just have to make a correct prediction of a price movement in a certain amount of time (expiry time). The conditions for traders and investors have to be checked before signing up with any broker. For example, it is very important for a binary trader to get the chance of high yields in assets from the broker.
Furthermore, it is important that offers, bonuses, and assets are available. In my Quotex (qxbroker.com) review, I checked every detail and will show you the results.
Quick facts about the offers:
| Minimum trade amount: | $ 1 |
| Maximum trade amount: | $ 1,000 |
| Trade types: | Binary Options, digital options |
| Expiration time: | 60 seconds up to 4 hours |
| Markets: | 100+ |
| Forex: | Yes |
| Commodities: | Yes |
| Cryptocurrencies: | Yes |
| Stocks: | Yes |
| Maximum return per trade: | 95%+ |
| Bonus: | Up to 100% for deposits, contests 50% deposit bonus with code: ‘BObroker50’ |
| Execution time: | 1 ms (no delays) |
(Risk warning: Your capital can be at risk)
Quotex minimum deposit and trade amount: How to start investing
When you want to start with Quotex you have to deposit at least $ 10. The minimum deposit is $ 10 but can verify by the deposit methods. There are different payment methods available which are depending on your country of residence. For example, traders from Europe can use other payment methods than traders from the USA.
To give you some insights: If you’re a European trader and want to use the cryptocurrency Ripple, you need to deposit at least $ 50. If you’re using MasterCard, the minimum amount is just 10 $. This minimum deposit is very low compared to other online brokers and trading platforms. It is easy to start with $ 10.

Also, the minimum trade amount is only $ 1. You can start trading with small amounts of money. I recommend it for beginners to just start with $ 1 and see how it goes. If you do not want to invest real money directly you can use the free demo account filled up with $ 10,000.
Assets and markets
Quotex offers to trade:
- Currencies (forex)
- Cryptocurrencies
- Commodities
- Stock Indices
- (weekend trading is available via OTC charts!)
As mentioned before, Quotex is a very new online broker. The management will upgrade and develop the trading platform step by step. They plan to add more assets for trading to the platform. Just go to the menu, and you can choose the asset you want. Currently, you can trade and choose over 100 different markets.

(Risk warning: Your capital can be at risk)
How much money can you earn with the QX Broker? – Yield (profit)
The yield of one trade is limited up to 95%+. For example, if You invest $ 100 in the EUR/USD and make the right prediction of the movement, you will earn $ 195. The yield is depending on the asset, expiry time, and account level. If you are a VIP-Member like me, you can get an additional 4% profit on every trade.
There are several trading strategies. Personally, I recommend trading on the main stock exchange hours and using liquid assets for investments. These are the markets where you will get the highest yield. But you will see it by yourself if you go on the platform.
- Yield (profit) up to 95%+ per trade
- The profit depends on the asset and market situation you choose
- The profit depends on the expiry time
Expiry time
Binary Options (digital options) are limited to an expiry time. Some brokers offer you to trade only 60-second trades or 5-minute trades. The expiry time is always depending on the broker and what he is choosing to offer to the clients. With Quotex.com you are very lucky. You can choose expiry times between 60 seconds and 4 hours. Everything between is possible. For example, you can choose an expiry time of 2.30 minutes.

Quotex (QX Broker) bonus explained
A bonus is free, and additional money is in your account. The broker gifts your virtual money for trading. But it is not completely free because you need to a turnover (volume) based on the bonus. The bonus amount has to be multiplied by x100. The result is the trading volume you have to do on the platform before you can withdraw the bonus. It is possible to get a bonus by depositing money or using a Quotex promo code.
- Bonus up to 100%+
- The bonus can be deactivated at any time
- The bonus turnover is x100 (before a withdrawal is possible)
Get a free deposit bonus of 50% with our promotion code “bobroker50“
Quotex promo code for free bonus
The promotional code allows you to get a higher bonus even if you deposit only $ 100. With my promo code, you will get a 50% free bonus. Pay attention because the promo code is limited to up to 25 new traders:
Quotex platform Promo Code: “bobroker50“
(Risk warning: Your capital can be at risk)
Trading fees: How much does it cost to trade on Quotex?
Let me tell you one of the best things about the Quotex platform: There are no fees no matter what you are doing or which asset you’re trading on the platform. This binary options broker doesn’t charge you any fee.
There are no deposit and withdrawal fees. You can start trading and top up your account without being charged. Also, you don’t have to pay a fee for trading the several assets that are available. Some brokers charge an inactivity fee. What does that mean? If you’re not login to your account for a long time, the platform will let you pay for that. Quotex doesn’t belong to this sort of broker, and you won’t pay an inactivity fee.
Test of the Quotex trading platform
As your read before, the trading conditions are very competitive and better than most other Binary Options Brokers. Now, I will go into detail and show you the trading platform. I tested the software for many weeks and traded it with real money on it. I will show you the results, features, and how to use them correctly. After this test, you will know what Quotex is all about.
The following platforms are available:
- Web Trading platform for a desktop computer or mobile devices
- Android mobile app (apk)
- iOS (iPhone) mobile app (not at the moment due to my research)
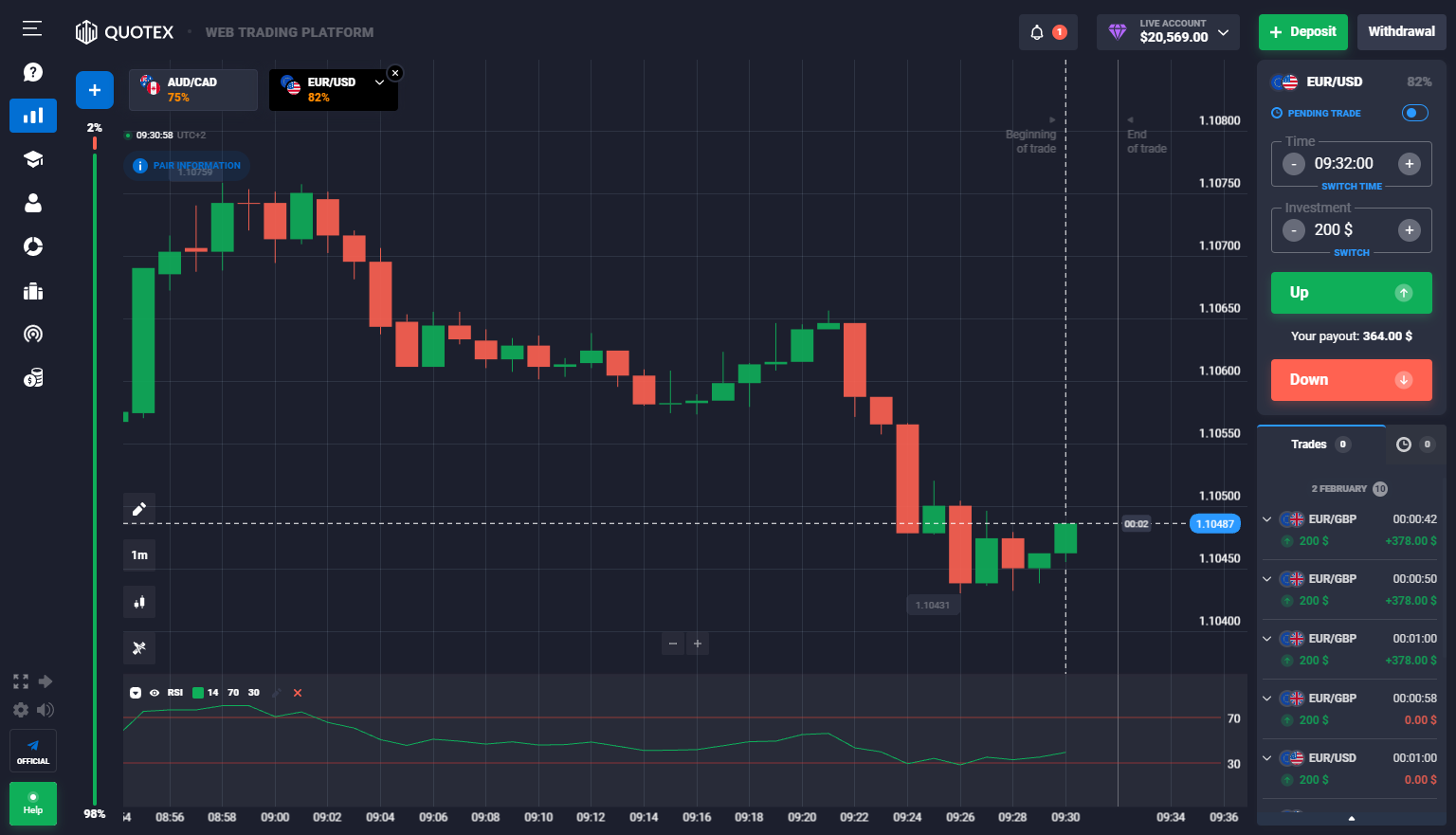
See a screenshot of the Quotex trading platform:

In the picture above, you see the Quotex trading platform for desktop devices. You can use the platform in your web browser (chrome, safari, opera, internet explorer, and more). In the next sections, I will show you the features of the platform and trading account.
First of all, you will see a random chart after your login into the platform. On the left side, you will find the sections about your account, education, tutorials, financial status, and trade signals. It is a typical menu where you manage your account.
Check out my video about the platform:
For changing and analyzing the asset, you can click on the asset menu:

Choose the asset you want to trade and start analyzing. It is also possible to do multi-charting. You can open more than one chart at the same time and switch between them.
(Risk warning: Your capital can be at risk)
Charting and analysis
To trade binary options successfully, you have to do a correct forecast of the price movement. Most professional traders use technical analysis to generate trading ideas. Indicators, chart types, and different time frames are used for a professional technical analysis.
Quotex offers you a huge variety of tools to analyze the markets (including trading signals). You can choose more than 30 indicators, 4 chart types, and a lot of different time frames for analysis. Even technical drawing tools are available.

- Huge variety of technical indicators such as Bollinger bands, MCAD, or different oscillators
- Different chart types are available
- Every time frame is available
- Professional charting is possible
How to trade with Quotex: Trading tutorial – Open your Quotex trade
How to trade with Quotex? I will show it to you in the next steps. You can also watch videos on our youtube channel, binaryoptions.com where I am doing live trading. The next graphic will explain to you how to trade.

First of all, you have to choose the asset you want to trade and generate the trading idea (forecast of the price movement). Then you choose the expiry time of the trade. When should the trade end gain my profit? You will need a good calculation of your trading time. Then you choose the right trading investment (trading amount). The minimum trading amount is $1 with a Quotex trade. I recommend using an investment that fits a regular money management strategy. That means you invest in one trade around 1-2% of your trading balance. After that, you choose the trade direction and start the trade. Wait till the expiry time is over to collect the profit or loss.
For further information, you can read our guide to avoiding losses with Quotex.
5 steps to place a trade on Quotex:
- Choose the asset you want to trade
- Choose the expiry time from 60-seconds up to 4 hours
- Choose the investment amount (minimum trade amount is $1, maximum trade amount is $1,000)
- Choose the trade direction
- Wait for the end of the trade
(Risk warning: Your capital can be at risk)
Mobile trading via Quotex app
Quotex offers a mobile phone app for both common systems, Android and iOS. So, whether you have an iPhone or a smartphone that runs with Android: You can trade via the Quotex app from wherever you are. Both apps work the same way.

Have a look at the screenshot above. As well as you trade via the desktop version, you can trade with the Quotex app. Select the asset you want to trade; then, you will see the chart in the middle of the phone – it doesn’t matter if you’re using landscape or portrait format.
If you’re using the portrait format, you can find the expiry time, the investment amount, and the two buttons (Up and Down) at the bottom of the screen. To trade, just set the time and amount and choose whether the price goes up or down.
How do you download the Quotex app and start trading?

To download the app, you can simply search for “Quotex – Online Investing Platform” on your phone. Then click on Install to complete the download. After that, you need to follow a few steps to register through the app:
- Enter your email ID and create a strong password for security. Do not share the password with anyone else
- Then you can choose a currency to make deposits
- After making deposits, read the service agreement and click on the register
You will then see a section that says “trade on the demo account.” Click on it to make demo trades. And once you are ready, use real money to make actual trades.
Can you use trading robots on Quotex?
Quotex robots are not allowed on any platform (web and mobile app). Your trading account can get banned by using external software. Furthermore, external software can be a fraud to your trading account and account balance. Be very careful because you can get scammed easily.
(Risk warning: Your capital can be at risk)
How to trade different assets on Quotex:
The platform offers different assets you can trade. Let’s have look at common assets and if they can be traded through Quotex.
Can you trade Forex on Quotex?
No, it’s not possible to trade Forex on Quotex. You can only trade Binary Options with currency pairs as an underlying asset!
Can you trade Binary Options on Quotex?
You might know the answer: Of course, you can trade binary options on this binary options broker. To trade you just have to select the asset, set the expiry time and investment, and tell the broker if the price goes up or down.
Can you trade cryptocurrencies on Quotex?
Yes, there are several different cryptos available for trading. A little excerpt: Litecoin, Bitcoin, Ripple, or Ethereum can be traded.
Can you trade stocks on Quotex?
You can trade stocks on Quotex, yes. Many different stocks from all over the world are available. You can select companies like Microsoft, Boeing, or Intel as well as indices like NASDAQ, Dow Jones, or foreign ones like the Nikkei or DAX.
How to open your trading account with Quotex
To register with Quotex you need only your email address and a secure password. At first, you can start trading without verification.

The broker may ask you to upload your ID card if you want to deposit or withdraw huge amounts of money. To upload your documents open your personal menu and switch to “Account”. In the account menu, you can fulfill the required fields with your name and address by clicking on “Upload Documents.”
(Risk warning: Your capital can be at risk)
Account types on Quotex
Quotex offers three different accounts besides the demo account, which I will introduce you to later. The three account types are:
- Standard account
- Pro account
- VIP account

To verify your standard account, you have to deposit at least $10 which will help you access a few asset options for trading. This account type is recommended for beginners who don’t invest large amounts of money. You don’t have to do anything – just deposit the minimum of $ 10 and start trading.
If you’re feeling good and if you’ve earned your first money, you can move on to the pro account. To access it you have to deposit at least $ 1000. You will have some premium benefits as a part of the standard account features.
Is this not enough for you? Then move on to the professional account level. For experienced traders, Quotex offers its VIP account. You have to deposit a minimum of $ 5000 to reap these benefits.
Quotex demo account: The best way to practice trading
When it comes to practicing trading, you should use a demo account. Especially for beginners, it is a good way to learn the investment. You can also test the trading platform, gain knowledge, or test new trading strategies. Even professional traders are using a demo account to become better traders.

The trading platform offers a free demo account with virtual money of $10,000. You can refill the account balance every time you want. It is easy to switch between your real and demo accounts. It is just one click in the menu. I recommend using the free demo account first to learn more about the trading platform. If you are secure and sure you want to trade, you can invest real money or start with small amounts of $1. The demo account is available without registration.
(Risk warning: Your capital can be at risk)
Quotex login: It is very secure and simple
To start trading you have to login into the web platform or the mobile app. You just need your email address and password. I recommend activating the 2-factor verification on the login and withdrawal.

You will get a security code via email or SMS. That is an important security feature, and you should use it. The broker uses different URLs for its service:
(Risk warning: Your capital can be at risk)
Quotex verification: What you need and how long it takes
If you want to verify your account (you can trade without also with some restrictions), you have to prepare some documents.

At first, you have to click on your personal settings and switch to the tab “Account.” After that, you press the button “Upload Documents.” You will need the following:
- A copy of your passport’s first page
- A selfie for photo identification
- Proof of the present residential address to confirm
Once you’re done with that, it takes around 2-5 business days until Quotex completes the verification.
Available payment methods for deposit and withdrawal
If you want to start trading, first, you have to deposit money into your trading account. Fortunately, Quotex offers a lot of different payment methods. Let’s see what ways are offered for the deposit and withdrawal of your money.
How to deposit money – Deposit methods
In the menu, you can click on deposit funds, and you will come to the deposit methods. It is very easy to deposit money with Quotex. There are no additional fees, and the deposits are instant. You can choose between Credit Cards, cryptocurrencies, and e-wallets. The minimum deposit is $10, and the payment methods depend on your country of residence.
After clicking on the deposit method you like to use, you can choose the amount and a deposit bonus of up to 35%. I talked before about the bonus in this review. Insert your data and start the deposit.

Facts about the deposit and deposit methods:
- The minimum deposit is $ 10
- Credit Cards/Debit Cards (Visa, MasterCard, and more)
- Online bank transfers are available
- Cryptocurrencies (Bitcoin, USDT, Ethereum, Ripple, Zcash, Binance Coin, and more)
- E-wallets (Skrill, Neteller, ADVCash, Perfect Money, Piastrix, and more)
- The payment methods depend on your country of residence
Are there any deposit bonuses?
This is an interesting question. Why? Because I can offer you a unique bonus code that only works via this website. If you’re a newbie and getting started with trading binary options, you can use this code to boost your initial deposit.
Just use the promotion code “bobroker50” to get a free deposit bonus of 50%.
Get a free deposit bonus of 50% with our promotion code “bobroker50“
(Risk warning: Your capital can be at risk)
How to withdraw money – Quotex withdrawal methods
If you found your profitable trading strategy and want to withdraw money from your account or profits, just click on the menu and choose “withdrawal”.
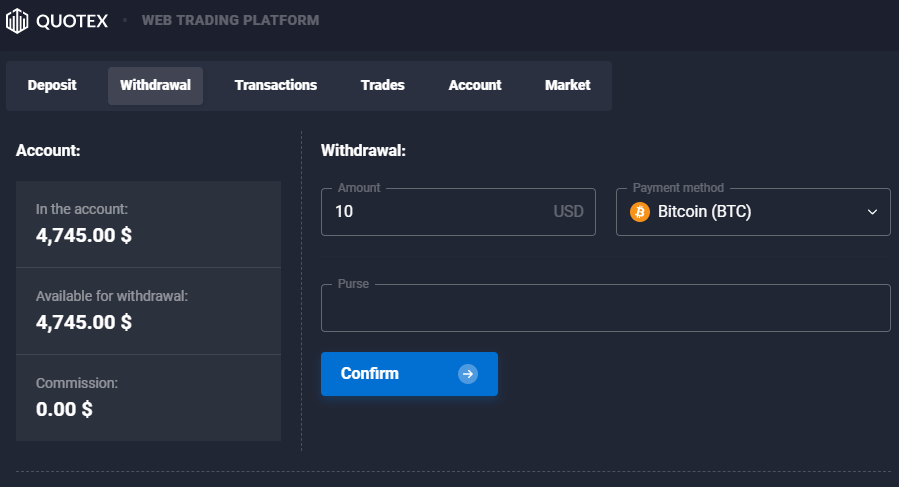
On the left side, you the how much money is available for the withdrawal. The bonus amount might affect these numbers. For withdrawals, you have to choose the same method as you deposited.
From my experience, the withdrawals are very fast. I did it multiple times, and Quotex is sending the money very quickly. Many traders are worried about it if the broker payout the profits. With Quotex you can be sure that the withdrawal is made securely and fast. In the next section, I show my withdrawal proof.
After requesting a withdrawal, you will get a confirmation message via e-mail:

- Incredible fast withdrawal methods (more or less the same as deposit methods)
- Secure and safe
- Maximum withdrawal/withdrawal limit: There are no withdrawal limits
- Minimum withdrawal amount: $10
In addition, read my full Quotex withdrawal review here.
(Risk warning: Your capital can be at risk)
My Quotex withdrawal proof:
Does Quotex withdraw money? – Yes, it does:

As you see in my menu, Quotex withdraws the profits. I did it several times, and there are no problems with withdrawing money. Also, I did some research on the internet, and there are no traders who are in conflict with this broker. For example, on Quora, you will find many positive reviews.
(Risk warning: Your capital can be at risk)
The Quotex marketplace explained:
Quotex has its own marketplace where Traders can get additional bonus features:

- Risk-Free trades
- Cashback
- Deposit bonus
- Percentage of turnover
- Balance bonus
- Cancel X Points
All these features are only available with a promo code. You may now ask how to get a promotion code? If you start trading real money with Quotex you will get free promotional codes after making a certain trading volume or depositing money. It is a very good feature for traders who invest and trade a lot of money. I can recommend this feature and it is completely free.
Get a free deposit bonus of 50% with our promotion code “bobroker50“
Special offer: Risk-free trades on Quotex

Every trader and customer on the Quotex web trading platform gets the chance of risk-free trades. The broker sometimes gives you discounts or promo codes for risk-free trades. If you are a high-volume trader, you will get a lot of benefits in the marketplace, as we discussed before. Furthermore, you can ask the support to get risk-free trades.
(Risk warning: Your capital can be at risk)
Professional offer: Quotex copy trading and signals
Another special offer of Quotex.io is the trading signals. It is also called “copy trading”. On the left side of the menu, you will find the section with “signals”.

Pay attention to the trading signals on the trading platform, and maybe you will get lucky to make good money on the market. You see the asset and the time duration of the trades. Unfortunately, there is no description or strategy for the trades. You do not know why it shows an up or down signal. It is maybe the result of technical analysis. For me, the signals are not transparent enough to use, but it is a good offer for new traders.
Customer service and support
Quotex offers 24/7 customer support in more than 20 languages. The support is available in English, France, Indian, Spanish, and many more languages.

There is a small disadvantage because Quotex does not offer phone support. It is only possible to get in contact with the broker via live chat and ticket support (email).
| Supported languages: | More than 20 offered |
| Live-Chat | 24/7 |
| Email: | Via ticket support |
| Phone support: | No |
(Risk warning: Your capital can be at risk)
Education material: How to learn trading with Quotex
If you are new to binary options trading, learning how the system and your favorite broker work is the most important thing. Don’t expect to get loads of money in your first days and weeks as a binary options trader.

To assist you, Quotex offers an educational section within its website you can use. In the FAQ, you’ll find all the answers to questions regarding the broker and its web trading platform. You can also watch my videos on the YouTube channel binaryoptions.com. I’m doing live trading and will show you the most important things to know when trading binary options.
Countries: Where is Quotex available?
Quotex accepts traders not from every country. There are different restrictions. On the payment methods, there are restrictions. Maybe you can not deposit or withdraw real money on the platform but you can use the free demo account for sure.
I also found this statement on the Quotex website: “The website services are not available in a number of countries, including USA, Canada, Hong Kong, EEA countries, Russia, as well as for persons under 18 years of age.”
Popular countries are Vietnam, Turkey, India, Indonesia, and Brazil. See the full Quotex country list here.
Are there alternatives to Quotex?
Quotex is the leading investment platform for digital options trading. But are there alternatives out there? On Binaryoptions.com I tested more than 40 different brokers and I can say that there are definitely alternatives. In the table below you will see the 2 most popular alternatives. If you want to find more alternatives visit this comparison.
| 1. Quotex | 2. Pocket Option | 3. IQ Option | |
|---|---|---|---|
| Rating: | 5/5 | 5/5 | 5/5 |
| Regulation: | IFMRRC | IFMRRC | / |
| Digital Options: | Yes | Yes | Yes |
| Return: | Up to 95%+ | Up to 93%+ | Up to 100%+ |
| Assets: | 100+ | 100+ | 300+ |
| Support: | 24/7 | 24/7 | 24/7 |
| Advantages: | Best trading interface | Offers 30-second trades | Offers CFD and forex trading as well |
| Disadvantages: | No phone support | No phone support | Not available in every country |
| ➔ Visit the Pocket Option review | ➔ Visit the IQ Option review |
To give you more alternatives you can visit the comparison between these other brokers:
Conclusion of the Quotex review and test: It is not a scam
Overall, Quotex is a reliable broker for trading Binary Options. It is not a scam for your money. I tested it several times to withdraw my profit, and also, on the internet, you will find only positive reviews about this platform. Quotex is a very good way to bet on the markets with limited risk and a high payout.
The platform for online trading is working very well and is user-friendly to use, as you saw in my review. I recommend using the demo account first before you deposit money. Furthermore, the minimum deposit is very low, and you can start with a minimum trade amount of only $1. Quotex offers you to make fast profits on the market.
Compared to other Binary Options Brokers, Quotex.io is number one at the moment in the market. There are no restrictions and limits for your trading. The return (yield) of investments is very high, and the withdrawals are working fast. I can recommend this broker after my Quotex review!
Furthermore, if you do not like this broker, see Quotex alternatives here!
(Risk warning: Your capital can be at risk)
Frequently asked questions (FAQs) about Quotex:
Is Quotex regulated?
Yes, Quotex, which belongs to Maxbit LLC, is regulated by the IFMRRC (International Market Relations Regulation Center) with the license number TSRF RU 0395 AA V0161. It is not a regulation of an official finance authority of a certain country.
Is Quotex a good broker?
Yes, Quotex is definitely a good broker. I tested this platform for many months and can tell you that there are no issues with it. The yield can be very high, up top 95%+ and you get a very fast execution of your trades. The software is working perfectly. Moreover, the withdrawals are very fast, and there are no fees for your payment transactions.
Is Quotex available in the USA?
Yes, Quotex is available in the USA. But there are maybe restrictions on the deposit and withdrawal methods and also the verification process. Please check with your regulation authority in your country if it is available or not. The free demo account is definitely available for everyone.
Is Quotex safe or not?
Yes, Quotex is definitely a safe broker for your funds. Deposits and withdrawals are working without problems. I tested it several times to withdraw my profit.
Does Quotex have an app?
Yes, Quotex has an app that is available for Android and iOS users. It offers a user-friendly trading interface, availability of signals and indicators, and trading with a real account or with a demo account. Therefore, trading on the go is possible.
How long is Quotex withdrawal?
Withdrawal at Quotex is usually very fast. In most cases, the money is transferred to the bank account after one day. However, traders should plan for a withdrawal time between 1 and 5 days, as it always depends on the chosen withdrawal method. Funds are returned using the same method they were deposited.
Is Quotex real or fake?
Quotex is a reliable online trading platform. The Financial Market Relations Regulation Center regulates it. If ever this trading broker fails to pay the winnings, this financial body offers a compensation fund.
Beginners and professional traders can use it without the worry of getting scammed. It has several positive reviews online, proving that it’s a trusted and reliable mobile app to work with. But residents of certain countries might face an issue using it.
So, it can be said that Quotex is real, but there is always the risk of losing your money to scammers. So be aware and only use the official internet address (domains) of quotex.com

