Bangladesh is a country in South Asia and shares its borders with India. That is relatively underdeveloped and new to binary options trading. However, there are many people who are frequently asking themselves if binary options trading is legal in Bangladesh. Moreover, binary options trading is quite popular among people who are well aware of the lucrative investment method.
In the trading industry, Bangladesh has a very strong and large investment market. In just a few years, huge growth in binary options trading has been seen on the online platform. The main reason behind the growth is some interesting and attractive topics related to the practices of investment.

Although binary options trading in Bangladesh has shown considerable growth, many still have unknown and misunderstood perceptions. This region has newly introduced the trading of binary options. So, it has not developed properly in brokerage services offering and its associated rules and regulations.
While focusing on the legal system of binary options in Bangladesh, it is still in an undefined situation. But there is no specific law that has mentioned whether it is illegal or banned. Alternatively, it also contains some restrictions and rules related to its practices, which is arising lots of confusion and complications among the people regarding its legality.
Nowadays, people seek a genuine platform to trade safely using several strategies as binary options trading has generated many controversies. In such a case, we are here to provide you with some vital information related to the trading of binary options in Bangladesh.
What are Binary Options?
If you are looking for an exotic financial option, binary options trading in Bangladesh can be the best choice. A binary option is a financial option where you have to predict some of the possible outcomes out of two options. The two main binary options types are:
- Asset-or-nothing binary option
- Cash-or-nothing binary option

The demand for the binary option is growing due to the better investment results. When the traders are investing in the binary option, they have to predict the moving price directions. Likely, the traders can receive up to 95% of their investment in return.
The use of online binary options trading has brought a lot of opportunities for the Bangladeshi people. In a very short time, they can gain more profits out of it.
There are many beginners and expert traders who are rapidly getting attracted to binary options trading. Also, those who are often looking for better investment options or genuine platforms choose this right trading option.
Binary options trading has a high chance of risk factors like other trading options. So, whenever you are planning to invest in a binary option, you can take the help of the best-regulated brokers. It is entirely legal and safe to plan the trade with regulated brokers.
Many citizens of Bangladesh are having confusion about where to begin the process with a safe side. If you have any doubts and confusion regarding the binary trading option, this article will help you clarify the binary options trading in Bangladesh.
(Risk warning: You capital can be at risk)
Are Binary Options Legal in Bangladesh?
As mentioned above binary options trading in Bangladesh is in an undefined situation. But, you cannot say that it is an illegal practice as no specific law is pointing out this. Though it can be a bit confusing for many people, it can be considered legal and safe.

If you are new to the trading market, you have to understand the rules and regulations. And, accordingly, you have to make some strategies to invest in trading. Here, a trader can get the freedom to take action with the legality of binary options.
Moreover, it would be best if you had a smartphone or computer and stable internet connection to proceed further. Apart from that, you need to ensure that your user devices support trading accounts, offshore trading platforms, and trading deposits.
Why do expert traders Look for Binary Options trading in Bangladesh?
People are often looking for one method or way that can change their life and financial status. This one method can be the binary options trading in Bangladesh. In fact, expert traders have understood this.

Expert and skilled traders apply different strategies in binary options trading to get more profits out of it. They have a good understanding of the price direction of a specific asset, and accordingly, they apply their prediction strategy.
Traders know they can achieve up to 95% in their investment with their prediction, and they can also lose if the price falls in the opposite direction. So, accordingly, they purchase fundamental assets like GBPUSD, EURUSD, or USDJPY.
Moreover, expert traders always have an eye on the asset value. If the binary options are predicted to surpass the current pricing, the trader places the CALL option. And it should be placed before the close of the expiry period.
Similarly, when the experts think that the asset price would not increase compared to the current pricing, they can place the PUT option. Therefore, the trader has to be very attentive and active while the trade is on.
How to trade Binary Options in Bangladesh?
The whole binary options trading in Bangladesh depends upon the possibilities of probability with different strike prices. Here, you can take a risk to place a binary trade. Likely, it requires following up on some of the essential steps that can help you to trade safely.
(Risk warning: You capital can be at risk)
Step #1 Select A broker
In this binary options trading process, the most important thing to consider is selecting an offshore broker. A broker can help in choosing the perfect and safe binary options site for you. The broker’s views are important as he is an expert in this field.
Moreover, the brokers use some of comparison tools to provide you with the best option. Also, picking the best-regulated brokers is completely safe and legal in Bangladesh.
Step #2 Understand The Market Trends
The market scenario is not static, and it is always dynamic. Daily, the market trend changes, and you have to show some punctuality to be updated with the movement. You have to be updated with the current scenario and the past growth aspect.

In this trading market, the most crucial method of work is to observe and react. You need to watch the market financial events and their forecast period. Accordingly, you can predict and respond in trading.
(Risk warning: You capital can be at risk)
Another critical factor is that you need to look at the market economy. Its understanding will help you to predict better in binary options trading. Also, it is essential to understand the growth-affecting factors in the trading market like business developments, politics, international relations, economy, and others.
Step #3 Select The Market to Trade or The Asset to Trade
The selection of the market or the asset to trade in the trading market is a very crucial decision. After understanding the market trends, you will get some ideas to make the right choice. After the proper selection of the trading market, you need to stick your focus to that.
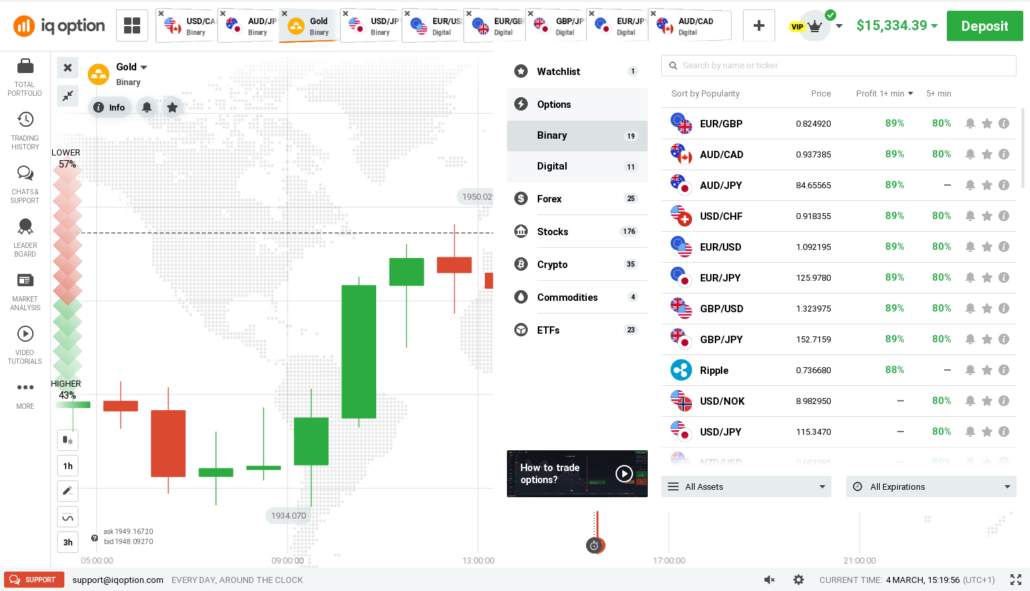
While choosing the market to trade, you need to check the contract durations and offerings of the right opportunities in the trading plan. Along with this, you can go for the industry of your personal interest. If you are not interested in some particular marketing industry, there is no point in going there.
(Risk warning: You capital can be at risk)
Moreover, the asset lists are always huge when looking for binary options trading in Bangladesh. It can cover cryptocurrency, commodities, forex or indices, stocks, and others.
Step #4 Select The Expiry Time
The trading of a binary option can look easy and simple, but it has a complex process. For this, you need to adopt some advanced strategies and plans as well as good predictions. And then, you can strike the cost.

Here, you have to use your analytical skill along with your researched marketing prediction. And, you must develop a “fear to lose” the trading price because the trading market can show many ups and downs.
In the trading market, you can get many options to choose from, which can be available for a certain period of time starting from 30 seconds and can be up to a year. So, it would be best if you considered the expiry time of the asset likewise.
Step #5 Set The Trade Size
Expert or skilled traders always go with their safe options. They never choose 100% investment in binary options trading because of the risk factor. So, you have to be very careful about the trading amount that you are investing in.
(Risk warning: You capital can be at risk)
Step #6 Click On the Button
After your decision over the trade size, you can jump into the clicking button. Here you can get options like Sell or Put or Buy or Click Call to place your order. Also, the option buttons vary according to the broker.

According to your personal interest, you can place a market order or limit order. But you have to keep an eye on the rise and fall of the asset value.
Step #7 Confirm The Trade
The last and seventh step is confirmation of the trade. Here, you can get immediate fill with the market order. But, it requires some time to fill in case of limit order. Well, you can get the chance to correct the details before the final submission of the trade. But it is not applicable to all brokers.
You might win and lose the trade on this platform, but you have to be very attentive. If you find your selected trade option is against the market, you have to take quick action to close it. And you can reduce the chance of losing the amount.
List of the 5 best Binary brokers in Bangladesh
Generally, there are many suitable brokers all over the world. With so many options, it’s hard to keep an overview. Therefore, we have chosen the best ones for you. So, let’s find out more about the best binary brokers in Bangladesh.
Best 4 brokers to trade with in Bangladesh:
See the best 4 Binary Options brokers in Bangladesh:
100+ Markets
- Min. deposit $10
- $10,000 demo
- Professional platform
- High profit up to 95%
- Fast withdrawals
- Signals
300+ Markets
- $10 minimum deposit
- Free demo account
- High return up to 100% (in case of a correct prediction)
- The platform is easy to use
- 24/7 support
100+ Markets
- Accepts international clients
- High payouts 95%+
- Professional platform
- Fast deposits
- Social Trading
- Free bonuses
100+ Markets
- Professional platform
- Free demo account
- $10 minimum deposit
- Webinars and education
- High payouts
100+ Markets
- Min. deposit $10
- $10,000 demo
- Professional platform
- High profit up to 95%
- Fast withdrawals
- Signals
from $10
(Risk warning: Trading is risky)
300+ Markets
- $10 minimum deposit
- Free demo account
- High return up to 100% (in case of a correct prediction)
- The platform is easy to use
- 24/7 support
from $10
(Risk warning: Your capital might be at risk)
100+ Markets
- Accepts international clients
- High payouts 95%+
- Professional platform
- Fast deposits
- Social Trading
- Free bonuses
from $50
(Risk warning: Trading is risky)
100+ Markets
- Professional platform
- Free demo account
- $10 minimum deposit
- Webinars and education
- High payouts
from $10
(Risk warning: Trading is risky)
#1. Quotex
Quotex is by far one of the best to use for binary options trading, and it has proven itself to be a breath of fresh air for traders. It is one of the best because of its diversity, reliability, and intuitive and user-friendly interface. Another interesting feature of Quotex is the ease and simplicity of withdrawal, and it gives about 70%-90% payment, and it supports cryptocurrencies, forex, and commodities.
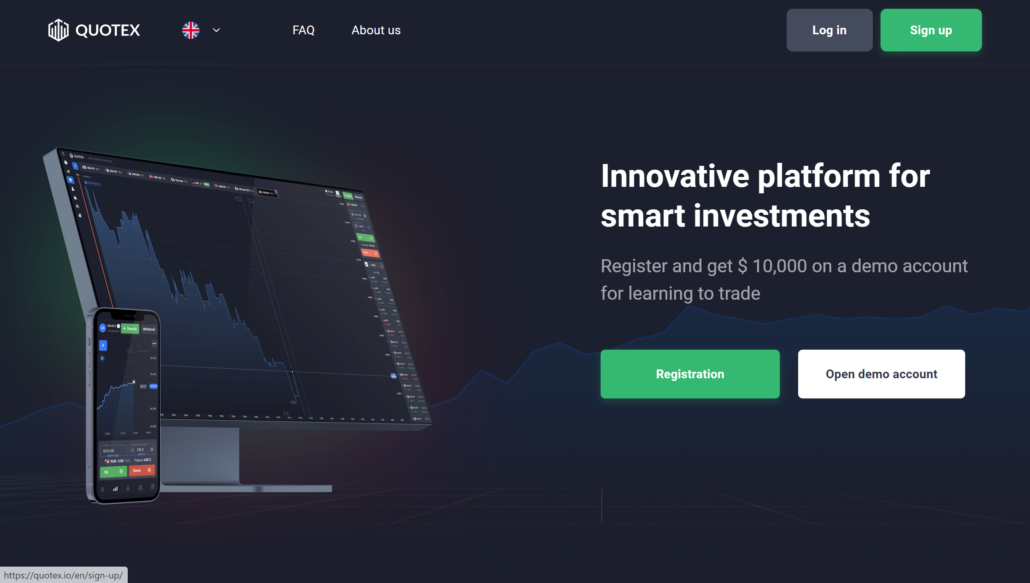
On Quotex, the live price feature is spot-on, accurate, and correct. Also, it’s important to mention its resourceful FAQs and responsive support.
Features:
- Minimum deposit: $10
- Minimum per trade: $1
- Leverage: 1:1
- Support mobile: Yes
- Demo account: Yes
- Founded: 2019
(Risk warning: You capital can be at risk)
#2. IQ Option
Another interesting broker to use in Bangladesh is IQ Option. It is one of the platforms with the lowest reviews. It supports credit, debit cards, and a host of other payment methods such as Skrill, Webmoney, Moneybookers, etc.
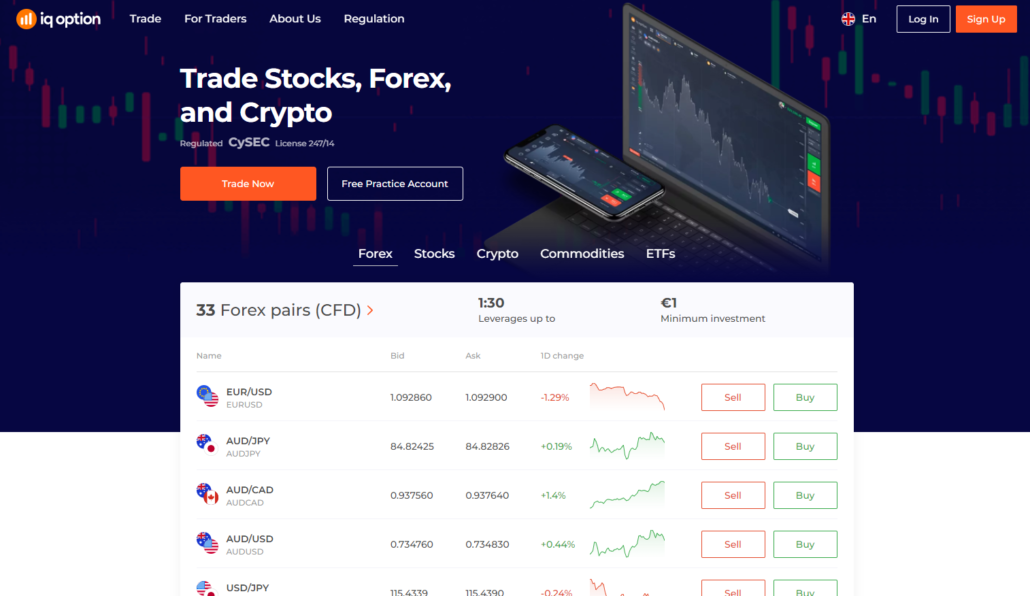
However, it is a regulated broker that supports cryptocurrency and forex, stocks, and option, and there is no option to use MT4 because they don’t have it. It is easy to use both on the desktop and the mobile app, and it is also user-friendly.
Features:
- Minimum deposit: $10
- Minimum per trade: $1
- Leverage: 1:500
- Support mobile: Yes
- Demo account: Yes
- Founded: 2013
(Risk warning: You capital can be at risk)
#3. Pocket Option
Pocket Option is another interesting option. It has over 100 assets on its portfolio, multiple payment options, and is regulated by the IFMRRC.

It can operate a demo account with no registration. Pocket Option is user-friendly and has generous payment, gives a bonus on registration, and supports stocks, options, indices, and commodities.
Features:
- Minimum deposit: $5
- Minimum per trade: $1
- Max leverage: 1:100
- Platform: MT5
- Demo account: Yes
- Founded: 2017
(Risk warning: You capital can be at risk)
#4. Olymp Trade
Olymp Trade is owned and operated by Saledo Global LLC in St. Vincent and the Grenadines.
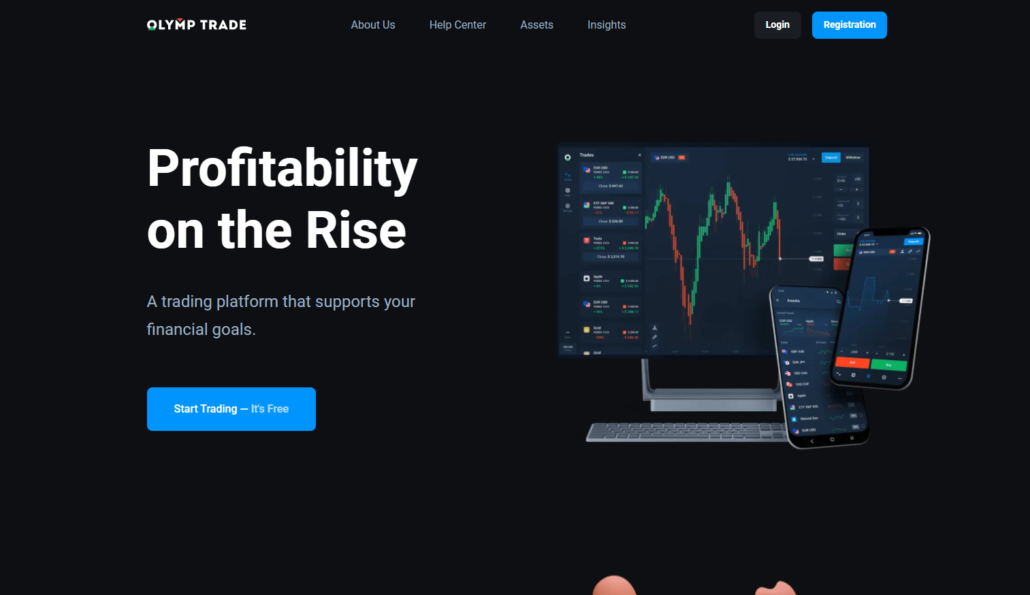
The platform is beginner-friendly. It hosts various programs to teach the user how to trade and make money trading. It is regulated and supports cryptocurrency, stocks, and indices.
Features:
- Minimum deposit: $10
- Minimum per trade: $1
- Max leverage: 1:500
- Support mobile: Yes
- Demo account: Yes
- Founded: 2012
(Risk warning: You capital can be at risk)
Regulations in Bangladesh
The Central Bank of Bangladesh was established in 1971, which has the main regulatory power of the financial markets. And, it also includes binary options trading. This bank works cooperatively with the government of Bangladesh to implement the regulations over the financial markets of the country.
Along with that, the Bangladesh Securities and Exchange Commission (BSEC) also works for the protection of brokerages and investors in the markets.
These two authorities have not mentioned that the binary options trading Bangladesh is illegal or banned. But, recently, the Central Bank has warned the traders to be careful and precise with the online trading of binary options. As it is not authorized by the Central Bank or any other authorities, many citizens of Bangladesh have confusion over its legality.
Education for Bangladeshi Traders
Online binary options trading in Bangladesh is not a simple process; you need to gather more knowledge and education regarding the trading market. This knowledge you can gather from various sources such as:

- Online Chat Rooms
One best places to learn about binary options trading can be the online chat room. Here, you can get more ideas about the trading market.
(Risk warning: You capital can be at risk)
- Beginner Guides & Newsletters
These newsletters and guidance for beginners are easily available online. And it does not require any special access or payment. Here, you have only to spend some time searching online.
- E-books
Nowadays, many E-books are available on E-commerce websites. Here, you can get valuable information related to binary options trading. Also, you can take the suggestions of your friends who are already involved in the trading market.

- Online Videos
The best and easiest way to understand binary options trading can be by watching online videos. Many conferences or seminars related to binary options trading can help you understand the trading market.

- Copy-trading
A beginner can adopt many strategies and ideas related to binary options trading through copy trading. You can follow some expert traders to get more information and implement it in your trading.
(Risk warning: You capital can be at risk)
Pros and cons of Binary Options trading in Bangladesh
The Pros of Binary Trading are:
- Low probability of significant loss – Even though binary options trading carries considerable risk, you have complete control over the amount of money that could be in danger. Most of the time, the contracts you’ll trade won’t seriously harm your finances, and you’ll be completely informed of your potential loss up front. The quantity of money you’re going to invest in the deal is up to you.
- Optimal risk management – With binary options, controlling your risk won’t be a critical concern right away. The risk level can be easily managed, monitored, and altered to suit your preferences. You can trade with several brokers for as low as $5 at a time, so you don’t have to risk hundreds of dollars if you don’t have the funds to do so.
The Cons of Binary Trading are:
- High-Risk Possibility – Generally speaking, you have control over the amount of money you trade, although larger payouts tend to come with greater dangers. Because market moves are unpredictable and there are frequently only a few minutes to make a trade, it can be difficult to know when to act. This might prompt riskier decisions. If you invest a lot of money in the transaction, likely, you won’t make a sizable profit.
- Limited Trading Resources – Many brokers won’t give you the tools and information you need to help and guide your decision-making. Due to the rapid speed and high level of risk involved in this type of trading, it can be simple to lose focus on the possibility of loss. If you don’t review the key performance indicators, you can end up in a bad financial situation.
Risks of Binary Options Trading in Bangladesh
Market Risk
Trading in binary options has a certain market risk, just like other types of investments. Markets can and frequently do change in unexpected directions with little to no notice in almost all circumstances. Even the most in-depth analysis often fails to precisely predict the precise course that the market will take, despite the fact that there are ways to anticipate probable market movements.
Profit Amount, Fixed or Capped
Fixed profits are a risk that traders of binary options should be aware of. There is no limitless upside possibility with these investments because both gains and losses are capped in the case of these investments. However, losses are also limited, which is a plus.
Extremely Accurate Profit and Loss Points
Binary options are also quantified by the tiniest tick, unlike many other forms of investment. As a result, this type of option’s value is frequently based on up to three or four decimal places. Even 0.0001 points in binary options trading can determine whether a trader is on the winning or losing end of an investment.
Conclusion
In Bangladesh, there is no legislation that states that trading binary options is unlawful, according to any of the above-mentioned agencies. Binary options trading seems easy but has more chances of losing it with the lack of trade marketing knowledge.

Here, it is essential to use your personal analytical skill to gain more profits. Along with that, the selection of the right platform can help you to gain more benefits. Therefore, you always need to keep yourself updated with the ongoing marketing trades.
Frequently Asked Questions:
What are the major advantages of Binary Trading in Bangladesh?
If you start searching for the advantages of Binary Trading in Bangladesh, then you will find a long list. However, the major advantages are the safety structure of the trade, its reward system, and the clarity of risk in trading.
Is Binary Options trading in Bangladesh Risky?
Yes, risk is always present in the trading market. In fact, it all depends upon your prediction. If you are investing 100% amount in trading, then you have lots of risks. This is because if your prediction fails, all your amount can go from your hand.
Will I get a profit by trading Binary Options in Bangladesh?
Well, gaining profits out of Binary Options in Bangladesh is not a cup of tea for everyone. If you have a proper understanding of the marketing trade and can manage the trading, you can gain more profits from it.
Are binary options permitted in Bangladesh?
Whether it is lawful or not is not quite clear. However, many investors in Bangladesh trade binary options, but the nation and its regulatory authorities do not generally accept them.
Does Bangladesh have laws governing binary options?
In Bangladesh, binary options are not regulated in any way. Regulating bodies, though, work to safeguard and control the financial markets that binary options are a part of.
In Bangladesh, how may I trade binary options?
You need to create an account after choosing a company that offers binary options trading. It is quite easy to do online in a few easy steps. For some businesses, opening an account does not even necessitate a deposit.
(Risk warning: You capital can be at risk)








